See how Apporto compares to today’s most popular virtual desktop providers.
Learn how Apporto helps enable a more secure mobile workforce with its Zero Trust Virtual Desktops.
See how Apporto compares to today’s most popular virtual desktop providers.
Learn how Apporto helps enable a more secure mobile workforce with its Zero Trust Virtual Desktops.
Although all these solutions make efforts to address the growing security concerns, they fall short of zero trust.
While VPN technology can provide online privacy through a private network accessed from a public internet access point, it fails to offer the security that today’s companies need. VPNs do not secure the most vulnerable part of a network - the end point.


The central location of a VDI solution can remove some security vulnerabilities. However, with the rise of bring-your-own-device to the remote working , these legacy-based systems cannot easily maintain the governance and security required. Significant resources are required to build and maintain new security protections on a VDI system.


The movement of operating systems, applications, and data to the cloud through third-party virtual desktop DaaS solution providers also attempts to address security concerns. While many DaaS vendors prioritize redundancy, backup and recovery protocols, and added security services for customers, they fall short of zero trust.

The next-generation virtual desktop that helps you achieve zero trust.


Securely deliver 24/7 access to the applications and resources they need, whenever they need it, from any device (BYOD) without the hassle of VPN. Anytime/Any Device/Anywhere Access
Apporto handles software deployment, backup, recovery, monitoring, antivirus, and more, all as part of the service. No packaging, complex configuration, or endpoint management is required.
A simple, all-inclusive subscription plan with no hidden fees or overages at a low predictable fixed cost.
Enable BYOD without the hassle of VPN or endpoint management securely with the backing of Apporto’s zero trust and least privilege security architecture.
Advanced compression, geo-optimization, and autoscaling deliver a true local-like user experience on Windows, Mac, and Linux.
Eliminate the need for server setups, datacenter overload, and patch management. Simplify and scale your infrastructure effortlessly.



Apporto provides a range of deployment choices tailored to your needs, including cloud-based, on-premises, or a hybrid solution. With compatibility across AWS, Azure, and on-premises systems, it ensures extensive adaptability and scalability for your IT infrastructure.
Experience an unrivaled user experience with Apporto’s cutting-edge compression technology that reduces latency, geo-optimization for improved location-based performance, and autoscaling to ensure steady efficiency regardless of fluctuating demand levels.
Manage operations smoothly with Apporto’s intuitive, browser-based admin console, designed to streamline administrative tasks and enhance control.
Rely on Apporto’s dedicated customer support team, which functions as an extension of your IT department, handling software deployment, backup, recovery, monitoring, antivirus, and more, ensuring seamless IT operations.
Enhance your VDI with Apporto’s Cloud Bursting, offering real-time, seamless scalability to the cloud for varied needs like temporary workforce management and project-based expansion. This solution ensures efficient remote operations and business continuity with minimal infrastructure, maintaining high productivity in all scenarios.

Enjoy direct access to desktops and applications via your browser, eliminating the need for downloads and installations. This approach guarantees seamless compatibility across different browsers and devices, significantly improving user convenience and efficiency.
Foster effective teamwork with Apporto’s Real-time Collaboration tools. Integrated chat and voice capabilities enable swift and engaging interactions, while screen sharing and desktop control make collaborative efforts seamless and interactive for everyone, irrespective of location.





Apporto’s Cloud Mounter easily integrates with leading cloud services like OneDrive, Dropbox, Box, Google Drive, and supports on-premises storage solutions. This feature facilitates effortless file access and management, allowing users to navigate, organize, and share files across different platforms efficiently.

Apporto’s cloud desktops deliver exceptional versatility, supporting multiple operating systems such as Windows, Mac, and Linux. This adaptability meets diverse computing needs and accommodates various user preferences.
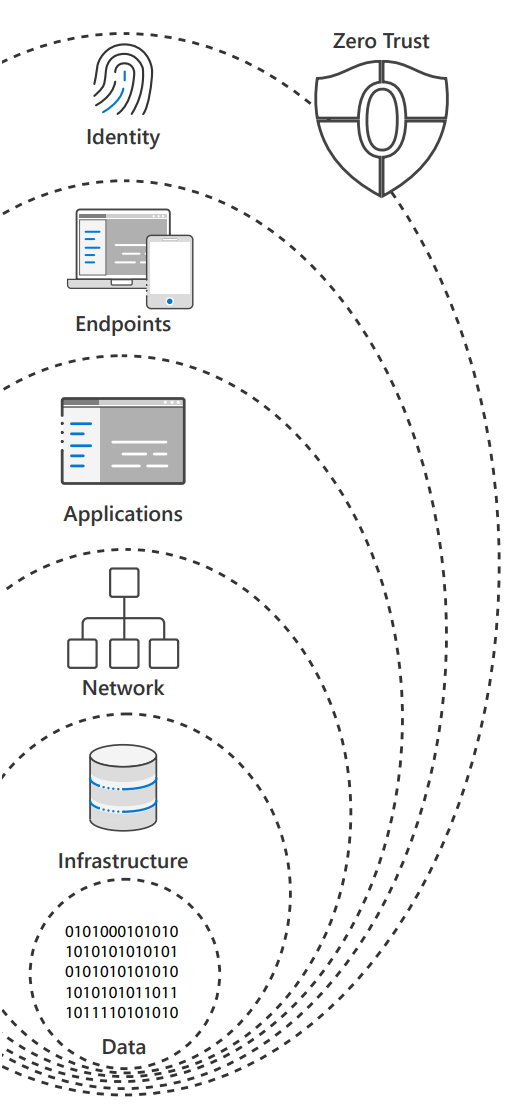
Zero Trust starts with identity, verifying that only the people, devices and processes that have been granted access to your resources can access them.
Next comes assessing the security compliance of device endpoints - the hardware accessing your data - including the IoT systems on the edge.
This oversight applies to your applications too, whether local or in the Cloud, as the software-level entry points to your information.
Next, there are protections at the network layer for access to resources – especially those within your corporate perimeter.
Followed by the infrastructure hosting your data on-premises and in the cloud. This can be physical or virtual, including containers and micro-services and the underlying operating systems and firmware.
And finally, protection of the data itself across your files and content, as well as structured and unstructured data wherever it resides